Does your team track emerging exploits across cybersecurity websites, code repositories, and social media sites?
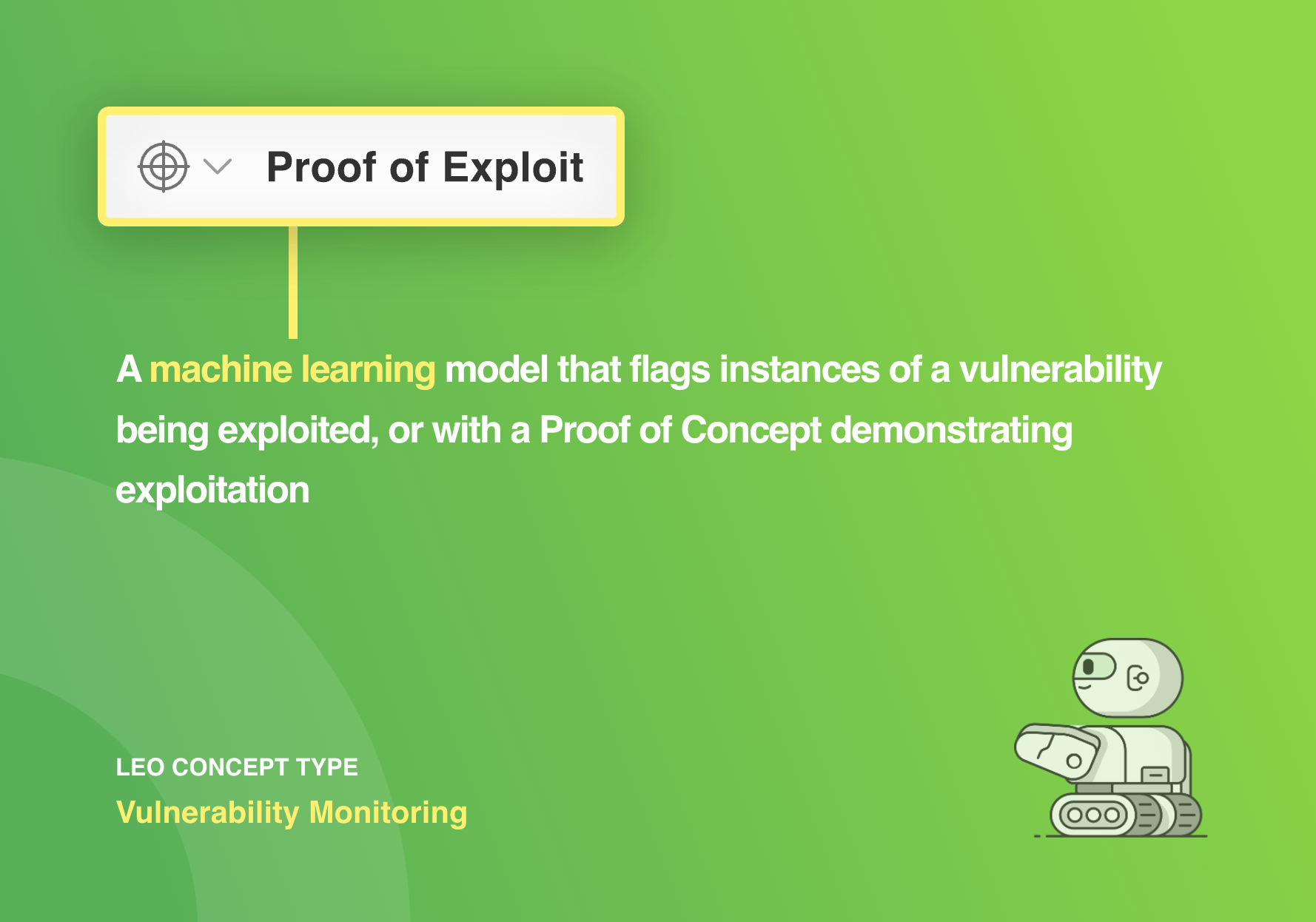
We just released a new Proof of Exploit AI Model that I think you will find valuable.
This new machine learning model allows you to:
- Discover proof of exploits early
- Research how vulnerabilities are being exploited
- Link exploited CVEs to adversary behavior
Curious how it works? Here is a tour


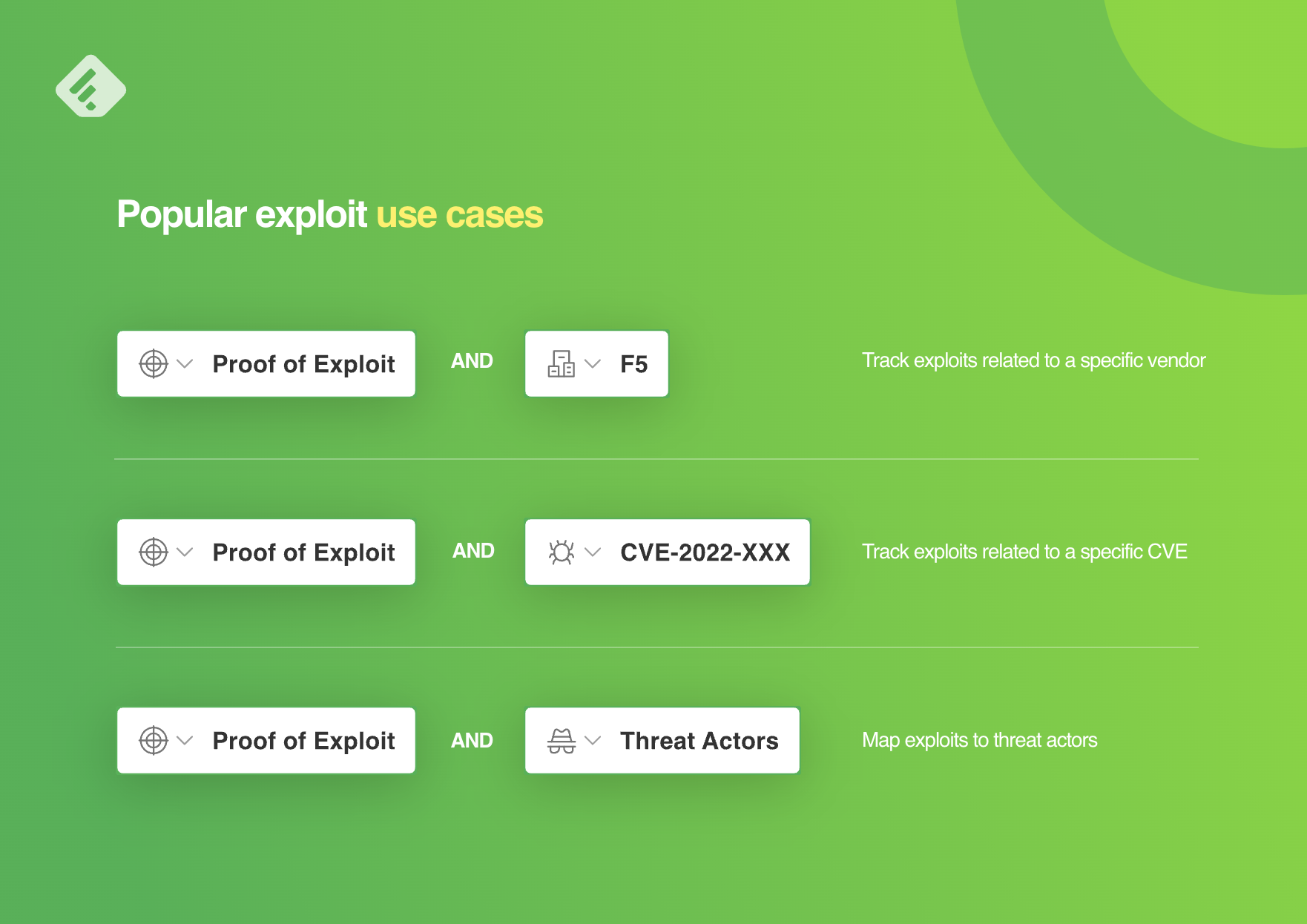
Speed up your cyber threat intelligence
Proof of exploit is one of the machine learning models included in Feedly for Threat Intelligence. Start a free 30-day trial to see how Feedly can help you speed up your threat intelligence.